Table of contents
Hello Iam Goutham in this blog I would like to explain what is VPC in AWS in beginner terms , how to setup and some networking terms.
What is VPC
Amazon Virtual Private Cloud (Amazon VPC) provides a logically isolated area of the AWS cloud where you can launch AWS resources in a virtual network that you define.
Through VPC we have a complete control of traffic that we have to allow in and out from the resources inside VPC.
With VPC including a selection of your IP address range, the creation of subnets, and configuration of route tables and network gateways are possible.
By default, AWS creates a default VPC per region.
There are some terms as beginners we have to know if we want to create our own VPC with our own network configurations.
Subnets
CIDR blocks or subnet masks
NACLS
Internet Gateways
NAT GateWays
Router and Route Tables
Subnets are the sub networks within network.
A CIDR block is a collection of IP addresses that share the same network prefix and number of bits. A large block consists of more IP addresses and a small suffix.
EX: If CIDR block is 15.3.2.1/16
Here each number separated by a dot is an octet and the first 16 bits won't change and we have flexibility with the next 16 bits and the total IP addresses that can be possible with this CIDR block are 2^16 as the last 16 bits can be either 0 or 1.
In this way, we can assign IPs to a network.
NACL also known as Network Access Control List is like a firewall for VPC through NACL we have flexibility in defining the traffic in as well as out through VPC.
The Internet gateway is used to allow external requests outside of VPC in to our VPC.
The NAT gateway is used to allow external requests outside of VPC in to private subnets and vice versa.NAT gateways hide the private IP of the resources from which it receives requests and expose its IP to the internet. NAT gateways use Elastic IP which means permanent public IP.
Router is a physical or virtual device that connect networks using route table in which target IP and destination network are metioned ,based on the route in the route table, router decides to which destination it has to forward the request.
Now let us build a VPC by using all the theories we have learned till now.
Let us build VPC having public subnet and a private subnet having EC2 instances and attach internet gateway and router to VPC , and a NAT gateway in public subnet to allow traffic to private subnet.
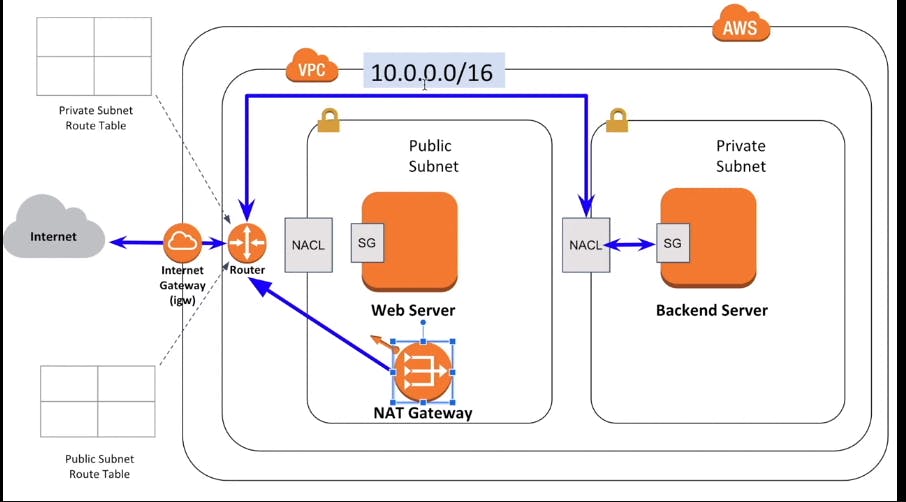
Image copied from Enlear academy youtube channel.
Let's first create our VPC by simply clicking on create VPC there are some rules to create CIDR block not particular but this is recommended choose
10.0.0.0/16 , 172.16.0.0/16 , 192.168.0.0/16
By /16 AWS provides the maximum possible IP address range, by /24 it provides the minimum address range but AWS reserves 5 IP address whose last bit is 0 ,1,2,3,255 in CIDR block if CIDR block is 10.0.0.0/16 2^16 IP address can be formed from that
10.0.0.0 , 10.0.0.1 ,10.0.0.2 ,10.0.0.2, 10.0.0.3 ,10.0.0.255 are reserved.
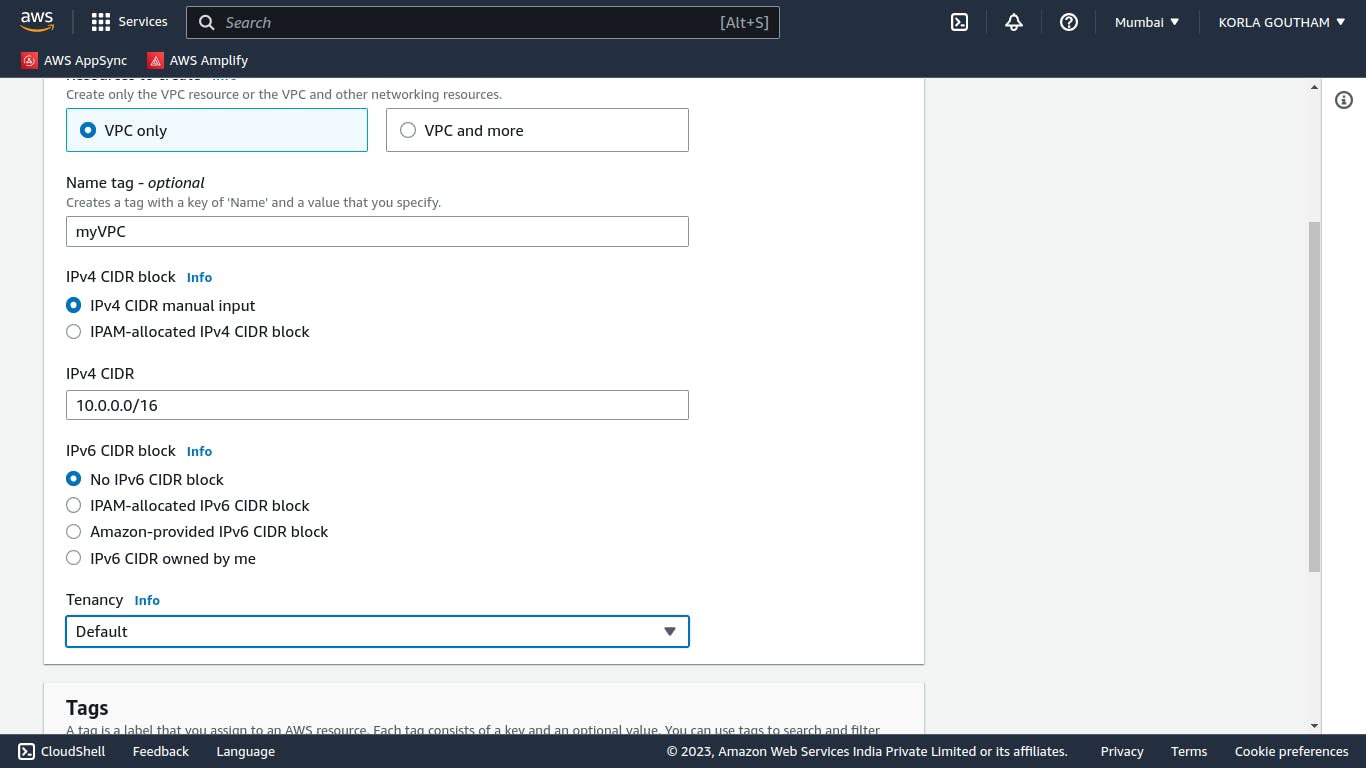
Now lets create subnet AWS provides 1 default subnet per region
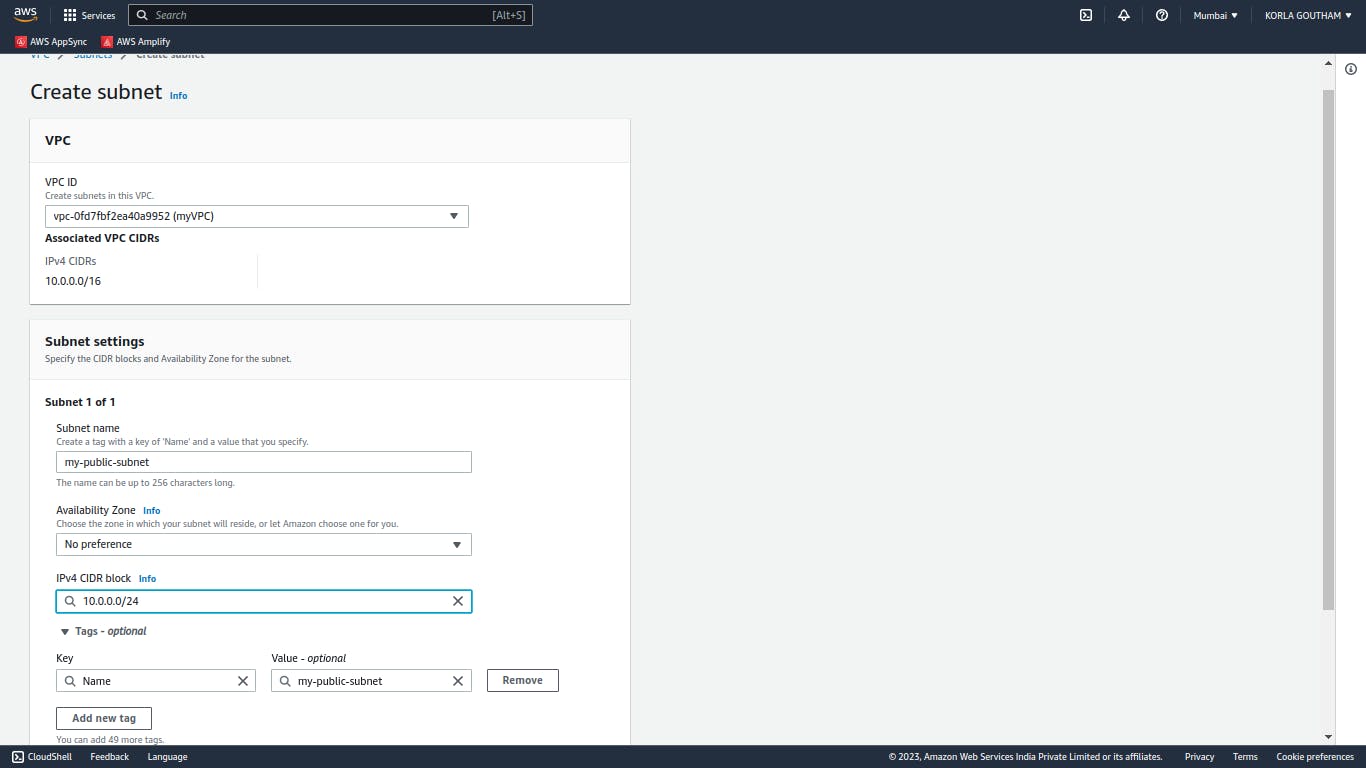
We have to choose CIDR block for subnet those IPs must be a part of VPC CIDR block and IPs of one subnet shouldn't clash with other subnets in same VPC.
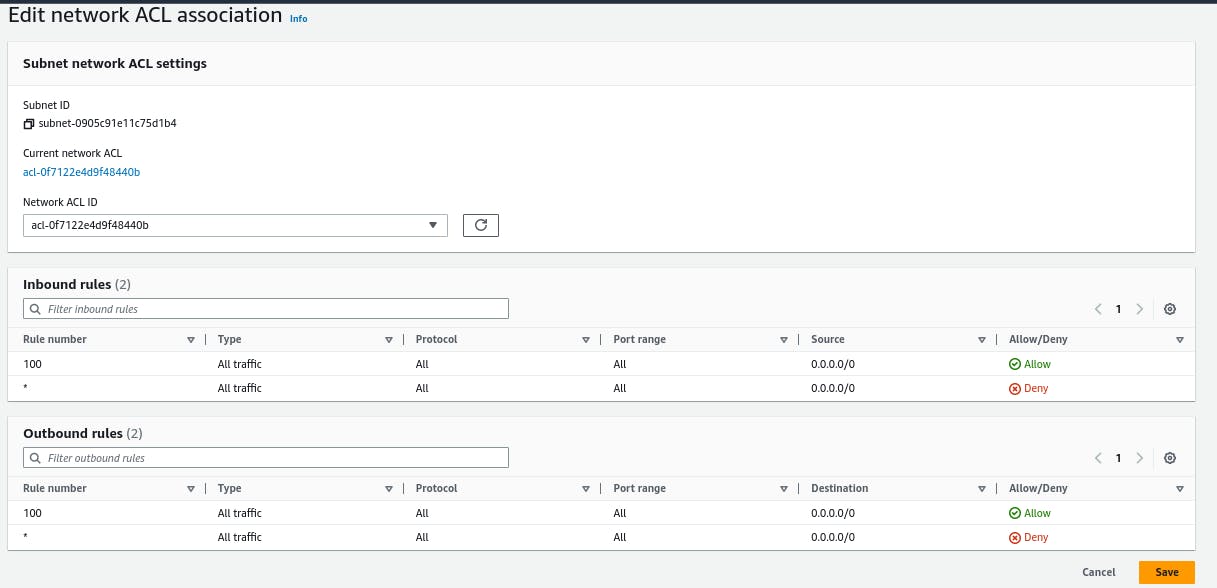
We can choose what type of traffic allowed and what denied in and out through VPC by NACLs least rule number has highest priority.
Now lets create private subnet in the same way but here we have to uncheck auto-assign public IP.
Now let's place EC2 instances in the subnets and allow all traffic to EC2 placed in public subnet.
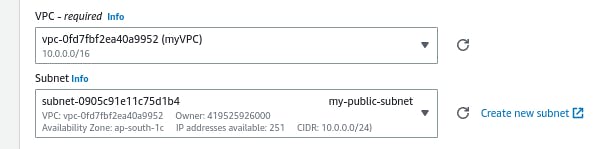
Now let's place other EC2 in our private subnet by allowing traffic only through public subnet as we dont want any public access . We can do this with security groups select traffic from security group attached to the instance in the public subnet.Now the instance in the private subnet receives traffic from the public subnet only.
Now let's create Internet gateway and attach to our VPC.
Create a route table and attach to our VPC , by default it has a route if the destination IP of the request is in the same range as of VPC then router forwards the request to the same network for any other routes we have to mention and attach to the subnet want.
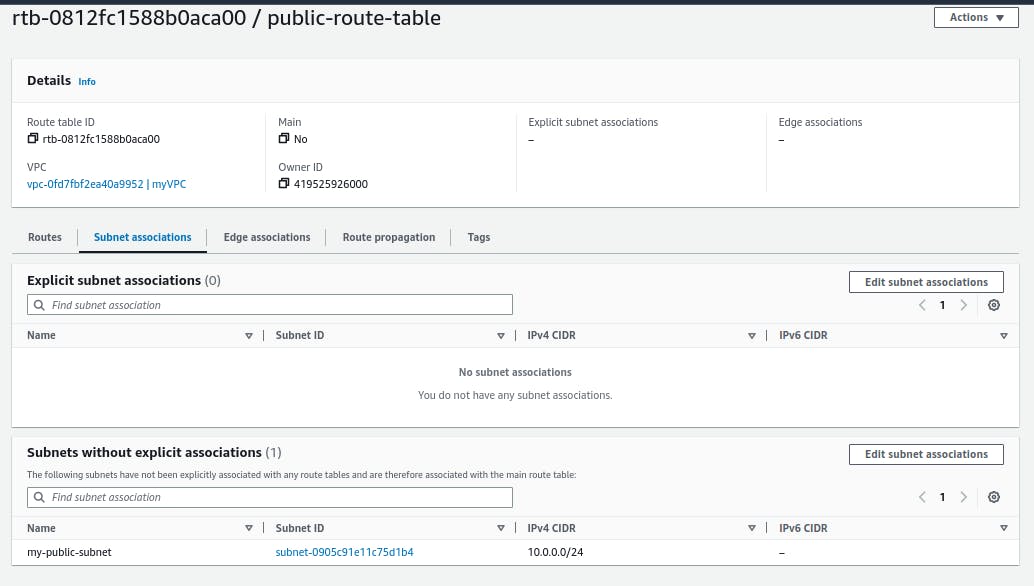
Click subnet associations and attach route table to public subnet and click edit route in the route table created , and add a route to internet gateway by
0.0.0.0/0 as target and created internet gateway as the destination which means any other request other than the IPs in the VPC has to route to the internet.
We have to create other route table for private subnet as instance in the private subnet must only receive from public subnet but if the instances in the private subnet requires internet then ? for that we use NAT gateways.
Lets create a NAT gateway and attach elastic IP and place NAT gateway in publicsubnet .
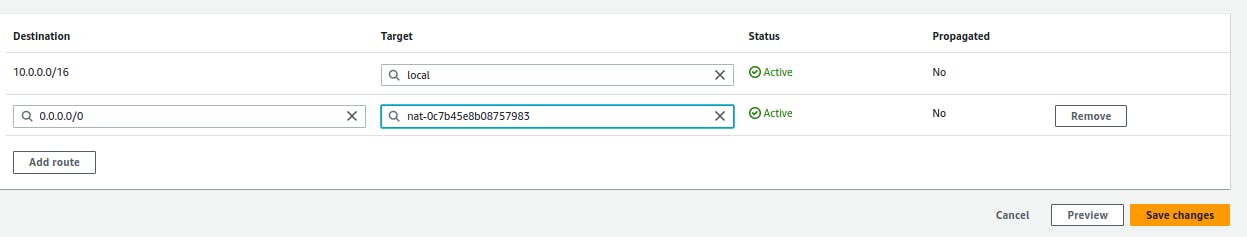
Now in the private route table add a entry to NAT gateway as
0.0.0.0/0 as target and NATgateway as destination.
Now we have configured everything let's test it...
ssh to the ec2 server in the public subnet
by ssh -i <.pemfile> ec2-user@publicIP and apply ping google.com whose IP is not in the VPC range and this works.. we have to allow ICMP protocol in security groups attached to ec2.
How do we ssh in to private ec2 which doesn't have public IP ? We have allowed traffic from public subnet server so after ssh to public subnet server we have to ssh to private server in private subnet using private IP.
How do we use the .pem file which is in local machine in the public server ?
There are 2 ways one is to copy .pem file of the private server and create file in public server and use it to ssh to the private server , The other one is using ssh agents private file (.pem) exists in the public server until connection persists. This is better method as private file doesn't exist in server.
1st Method
cat <.pem> // To display private key of the private server copy it
touch private.pem // To create a file
echo " <paste copied content >" > private.pem // copied content pasted here.
ssh -i private.pem ec2-user@<privateIP> // Now we can ssh to private server.
2nd Method
ssh-add -K private.pem //adding pem file to ssh agent
ssh -add -l // Displays all the files attached to ssh agent.
ssh -A <.pem file> ec2-user@publicIP // Now the .pem file which we have used to connect to public server is now in the public server using this we can ssh to private but this works if we have used same .pem file as that of public while creating private server.
In the public server
ssh -A <.pem filec2> ec2-user@privateIp // We are now in private server
Use ping google.com in private server this works as in the private route table assocaited with private subnet there is a route to NAT gateway which hides the private IP from which it received request and exposes its elasticIP (publicIP) to the internet and receives payload from internet through router and forwards it to private server which made request.
Haha completed thats all about VPC I know. If you find anything wrong please let me know.
Thanks for reading have a great day.🥳🥳🥳
